Ways to Monitor Your Ecommerce Site for Credit Card Fraud
[ad_1]
According to Michigan Retailer Association’s study of retail sales presented in its 2021 Buy Nearby Study, national ecommerce sales grew from 8.8 percent of total retail sales in 2017 to 10.7 percent in 2019, and then jumped again to 13.6 percent in 2020. Although this information is hard to delineate at a state-level, there’s no doubt that Michigan’s retail sector has likely undergone a similar transformation.
Amid the COVID-19 pandemic, adding ecommerce as a mode for selling has been critical for many Michigan retailers. Without it, more retailers would not have survived the pandemic.
As online sales grow, so does fraud
As much as retailers have benefited from ecommerce sales, online credit card fraud has jumped significantly across the U.S. According to LexisNexis, U.S. ecommerce merchants reported a 140 percent increase in fraud attacks since 2020. Furthermore, according to a recent article in Business Insider, card-not-present (CNP) fraud is predicted to grow by 14 percent in the next four years.
One of the most common ways cyber criminals get stolen credit card numbers is through the dark web. Most visit a website on the dark web and buy stolen credit cards in bulk with the goal of testing them to find the ones that work. In 2019, there were at least 23 million stolen credit card numbers for sale on the dark web. That number has only increased since then.
What does this fraud mean to your business? Think more chargebacks, penalties, lost revenue, and a new reputation among criminals that your business is an easy target.
I say this often: fraud prevention is a journey, not a destination. Cyber criminals are very sophisticated and they change methods frequently and often. There are, however, three actions you can take that will help you prevent fraud during a transaction. They can expose a potential credit card theft in the making.
- Do you take notice if your terminal experiences an EMV chip malfunction?
While most of this article is related to ecommerce, one of the ways that bad guys use stolen card numbers is via a face-to-face transaction that is not “dipped” into the chip reader.
Although most merchants use an EMV chip reader, terminals are set up to allow for transactions to be processed using a magnetic strip to accommodate older cards without chips, or cards with malfunctioning chips. This is the loophole that criminals are now exploiting.
If a bad guy has a good card number (and the associated information from the mag stripe), they can encode that on a legitimate card and then damage the card’s EMV chip. This will force your terminal to accept a swipe (with the stolen card number on the mag stripe, instead of the legitimate card number).
When they make a purchase, they insert the card in the chip reader, which will report an error because the chip cannot be read. Then, they will tell the clerk that they’re having problems with the EMV chip on their card and ask if they can complete the transaction by either swiping the magnetic strip or having the clerk key in the account number, bypassing the EMV chip reader all together.
Take note, you need to be vigilant with your staff about always using an EMV chip reader. The major card networks have clear rules about this. If a merchant allows a customer with an EMV chip credit card to make a purchase by swiping the card in lieu of using the chip reader, any chargebacks filed against the transaction will automatically be found in the cardholder’s favor.
Alert your staff to take note when this happens, especially if it is a high-ticket number such as jewelry, appliances, or a computer. If your EMV chip reader continues to fail, it may be time to upgrade your system.
- Does your website require a three-digit security code for all online transactions?
According to a 2021 Nilson Report on credit card fraud, the amount of money lost to card-not-present fraud in 2020 was six times greater than what merchants lost just one year earlier. Hence the need to make sure that any purchases made on your website require a security code.
A credit card security code, commonly known as the card verification value 2(or CVV2) is the three or four -digit code usually found on the back of a credit card. The CVV2 provides an added layer of security by verifying that the purchaser is in possession of the card.
To stay PCI compliant, you are not allowed to store CVV2 codes on your system. This helps in protecting customers from a data breach and makes it difficult for cyber criminals to get a customer’s CVV2. Not complying with global PCI Data Security Standards could result in hefty fines or even worse – the cancellation of your merchant processing access by the payment processor.
- Does your website include a CAPTCHA as part of the checkout process?
One of the problems that bad guys have is figuring out if the card numbers that they bought on the dark web are still active and “good.”
A common online technique used by criminals is access websites to test a group of stolen cards by conducting low-amount transactions, usually $1 or $2 to find the cards that are still active. This type of account testing is known as “card tumbling.” One of the major consequences of being a victim of a card tumbling attack like this is the substantial fees your account can occur if the scale of the attack is significant. Some examples of fees include authorization, clearing and settlement, interchange, and gateway transactions.
Anything you can do to slow down the process of getting an authorization attempt on a transaction keeps card tumblers at bay. This is where including a CAPTCHA as part of your online checkout process plays a critical role. According to Dictionary.com, the origin of CAPTCHA stands for “completely automated public Turing test to tell computers and humans apart.” It is a type of challenge-response test used to determine whether the user is a human or a bot. To pass the test, users must interpret distorted text by typing in correct letters into a form field. In the case of a re-CAPTCHA, the user is required to identify a set of objects in a photo.
Although CAPTCHAs receive their fair share of critics, they’ve done a tremendous job in protecting ecommerce sites from brute force attacks.
As mentioned at the beginning of this article, this process of protecting yourself is a journey, not a destination. It is something that you should be paying attention to regularly.
As always, if you have questions about this issue or any other merchant processing issue, please don’t hesitate to contact our customer service team at 800.563.5981
Use this Ecommerce Fraud Decision Tree graphic to help you and your staff spot suspicious transactions.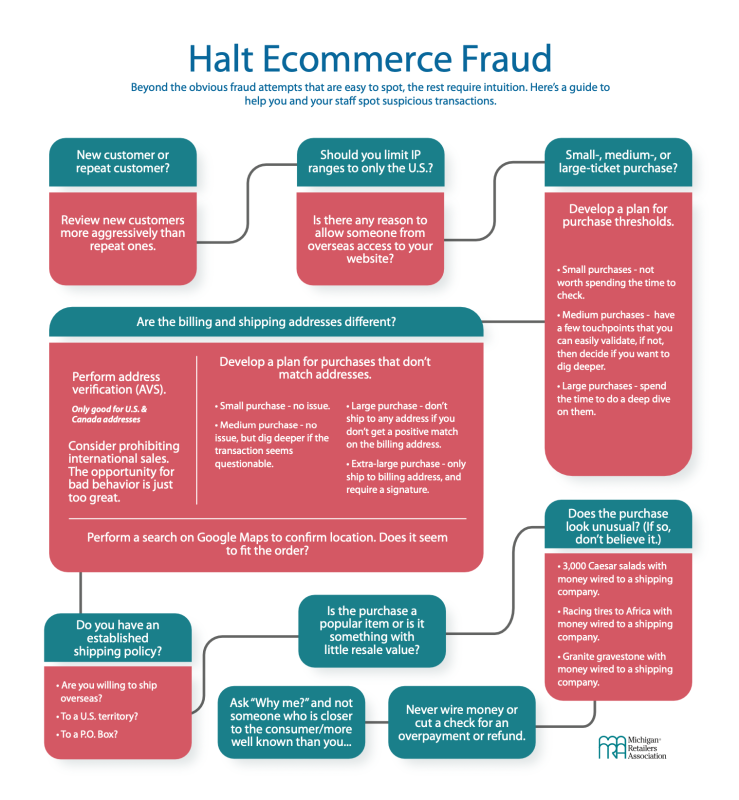
[ad_2]
Source link
